Informed means protected: IDBank
ՀԱՍԱՐԱԿՈՒԹՅՈՒՆ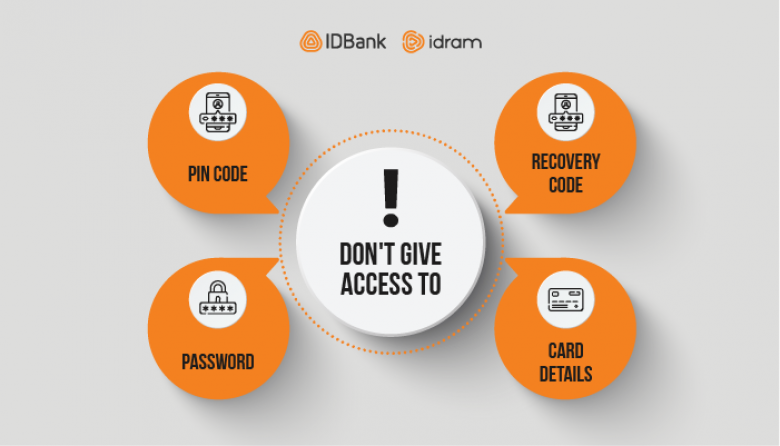
Did you know that in order to ensure your information and financial security, special subdivisions are operating in the Banks and payment systems, and huge investments are being made. Why? Because it is no longer fashionable to steal money stored under the pillow or in a hidden corner in the closet; nowadays there are more fashionable and effective methods which, however, will never come true if our society is informed.
What measures do counterfeiters now use to extort money from bank cards or payment systems? In order to receive answers to the questions we have talked to Armen Kirakosyan, Head of Information Security Unit of IDBank.
Informed means protected.
- Mr. Kirakosyan, we keep on talking about the fact that counterfeiters can extort money from people's accounts. Finally, what are the cases known, how are the thefts of the 21st century happening and what do your customers, users need to know in order to be protected?
- Information Technologies are evolving, same do hackers who are seeking for new ways to hack systems or steal certain data, and the most important values of the 21th century are time and data. Since the RA banking system is one of the most protected ones and we apply measures that meet all the global IS standards, in other words we do our best to have a stable, reliable and protected system, I would like to focus on cases when people become victims of deception without even imagining that by providing their personal data they, so to say, give the key to their house to a stranger. Let me describe a couple of cases:
- Counterfeiters open up false branches of the Bank, which, by the way, can bear a name and a logo barely differing from the Bank’s real name and logo, take out a loan through the real online banking on behalf of the client, but give the client, let’s say, 70-80% of the received amount. But the client bears the burden of the whole loan amount, doesn’t he? Now, it is very important to understand that no one can apply for an online loan on your behalf unless your personal data becomes known to him/her in this or that way.
- Counterfeiters visit people's apartments, register their data under the name of a charitable initiative, register them in the Bank’s mobile application with their phone number, even take photos on the spot, go through identification and again apply for a loan on behalf of those people; in this case the real borrower does not receive a cent, the counterfeiters just leave the apartment only after transferring the whole loan amount to their account. In other words, people provide their smartphones and personal data to strangers.
- Counterfeiters contact users by phone or social networks and say, for example, that a draw is planned to be conducted and that a certain amount will be transferred to their account in case if they win. Under that pretext, they, again, register people in the mobile application of the bank, perform the abovementioned actions. Of course, no draw is being conducted, moreover, people earn a loan burden about which they have no idea until after a certain period when they receive a notification from the Bank about making a payment and if no payment is made they appear on the blacklist.
- There are cases in the social networks as well when users receive messages from their friends’ hacked accounts and are being asked to make an urgent money transfer. This is another form of deception.
In fact, there are many options since, as I have already mentioned, counterfeiters seem to have plenty of imagination and risk, however the “Informed means protected” principle can definitely protect us.
- How can citizens protect themselves in the cases that you mentioned?
- In the 21st century a lot of life processes happen with the application of new technologies. Therefore, not only in the abovementioned but also in many other cases in life in various processes, in general, the adherence to the basic information security hygiene rules can help us, you only have to:
- Not provide the Bank code, password, PIN code, bank application password, code etc. to anyone, even to your close relatives. Remember, that all these are the keys to your apartment.
- Not allow anyone to perform any actions with your phone, especially download an application, take a picture of yourself or your documents etc. A smartphone is an important carrier of information nowadays and it must be protected with a password.
- Apply for a loan only in person and only to the Bank by personally downloading the Idram&IDBank mobile application, going through remote identification in person and applying for a loan in person or do all the same by visiting the branches of the Bank the addresses of which can be found on the Bank’s official website.
- Find out about the draws held by the Bank or Idram Company only through the official channels of communication of the companies such as the official website, social networks, e-mail etc. In case of receiving suspicious letters, check their authenticity by calling the Bank or Idram.
- In case of receiving a request from your close friends through the social network about transferring money, make sure you check the information by calling your friend to find out whether or not it was really your friend who sent the request or his/her page has been hacked.
You can endlessly mention such useful tips; however, it is important to use the 21st century’s most effective way to verify the authenticity of information: doubt, compare, check. By the way, IDBank has launched an information campaign and you can find various videos on our social media pages which describe this or that case of falsification and advise how to deal with them. So, follow us on the social media pages and stay informed and protected.
COMPANIES ARE CONTROLLED BY CBA

 Այս մարդը վերջին ութ տարվա ընթացքում ինչ ուզել է, ստացել է Փաշինյանից։ Կա՞ կասկած, որ Փաշինյանի կառավարությունը, եթե վերընտրվի, սա էլ չի ստանա. Նարեկ Կարապետյան
Այս մարդը վերջին ութ տարվա ընթացքում ինչ ուզել է, ստացել է Փաշինյանից։ Կա՞ կասկած, որ Փաշինյանի կառավարությունը, եթե վերընտրվի, սա էլ չի ստանա. Նարեկ Կարապետյան  Մյունխենի «Բավարիան» հաղթեց «Վերդերին»․ Լեվերկուզենի «Բայերը»՝ «Սանկտ Պաուլիին»
Մյունխենի «Բավարիան» հաղթեց «Վերդերին»․ Լեվերկուզենի «Բայերը»՝ «Սանկտ Պաուլիին»
 Եղանակայնի վտանգավորության «դեղին» մակարդակ է հայտարարվել
Եղանակայնի վտանգավորության «դեղին» մակարդակ է հայտարարվել ՀՀ տարածքում ավտոճանապարհները հիմնականում անցանելի են
ՀՀ տարածքում ավտոճանապարհները հիմնականում անցանելի են
 Հորանջելու գաղտնի իմաստը. գիտնականները պարզել են սովորական ռեֆլեքսի գլխավոր գործառույթը
Հորանջելու գաղտնի իմաստը. գիտնականները պարզել են սովորական ռեֆլեքսի գլխավոր գործառույթը
 Եղանակայնի վտանգավորության «դեղին» մակարդակ է հայտարարվել․ ՌԴ
Եղանակայնի վտանգավորության «դեղին» մակարդակ է հայտարարվել․ ՌԴ
 Հայ և ադրբեջանցի փորձագետներն ամփոփել են «Խաղաղության կամուրջ» նախաձեռնության արդյունքները
Հայ և ադրբեջանցի փորձագետներն ամփոփել են «Խաղաղության կամուրջ» նախաձեռնության արդյունքները Մեկնարկել է Հայաստանի շախմատի պատանիների առաջնության երևանյան ընտրական փուլը
Մեկնարկել է Հայաստանի շախմատի պատանիների առաջնության երևանյան ընտրական փուլը
 Հայ-ադրբեջանական համաժողովի քննարկումները կենտրոնացել են հայ-ադրբեջանական հարաբերությունների ընթացիկ փուլի վրա
Հայ-ադրբեջանական համաժողովի քննարկումները կենտրոնացել են հայ-ադրբեջանական հարաբերությունների ընթացիկ փուլի վրա
 Որպես իրավաբան՝ պարտավոր եմ մի քանի բան հստակ ասել Կաթողիկոսի նկատմամբ քրեական հետապնդման մասին. Թաթոյան
Որպես իրավաբան՝ պարտավոր եմ մի քանի բան հստակ ասել Կաթողիկոսի նկատմամբ քրեական հետապնդման մասին. Թաթոյան
 Ռոնալդուի 962-րդ գոլը նպաստեց «Ալ Նասրի» հաղթանակին
Ռոնալդուի 962-րդ գոլը նպաստեց «Ալ Նասրի» հաղթանակին
 Բայրամովը Գերմանիայի ԱԳ նախարարի հետ քննարկել է Հայաստանի հետ հարաբերությունների կարգավորումը
Բայրամովը Գերմանիայի ԱԳ նախարարի հետ քննարկել է Հայաստանի հետ հարաբերությունների կարգավորումը
 Փետրվարի 15-18-ը ողջ հանրապետությունում ջերմաստիճանը կշարունակի բարձրանալ
Փետրվարի 15-18-ը ողջ հանրապետությունում ջերմաստիճանը կշարունակի բարձրանալ
 Արցախցի այս կինն ապրում է անմարդկային պայմաններում. նա օգնության կարիք ունի
Արցախցի այս կինն ապրում է անմարդկային պայմաններում. նա օգնության կարիք ունի
 Մեր սահմաններին խաղաղություն է հաստատվում. Ադրբեջանն արդեն սկսել է համագործակցությունը Հայաստանի հետ․ Ալիև
Մեր սահմաններին խաղաղություն է հաստատվում. Ադրբեջանն արդեն սկսել է համագործակցությունը Հայաստանի հետ․ Ալիև
 Խոշոր ավտովթար` Երևանում
Խոշոր ավտովթար` Երևանում
 Իրանի նախագահը խոսել է տրանսպորտային միջանցքների եւ Ադրբեջանի հետ նմանությունների մասին
Իրանի նախագահը խոսել է տրանսպորտային միջանցքների եւ Ադրբեջանի հետ նմանությունների մասին
 Ձմեռային Օլիմպիական խաղերում լեռնադահուկորդ Հարություն Հարությունյանը գրավել է 59-րդ տեղը
Ձմեռային Օլիմպիական խաղերում լեռնադահուկորդ Հարություն Հարությունյանը գրավել է 59-րդ տեղը
 Հաղթում է անզուսպը, հախուռնը, խելագարը. Կաթողիկոսի դեմ քրեական գործ է հարուցվել, ի՞նչ անել․ Էդմոն Մարուքյան
Հաղթում է անզուսպը, հախուռնը, խելագարը. Կաթողիկոսի դեմ քրեական գործ է հարուցվել, ի՞նչ անել․ Էդմոն Մարուքյան
 «Տոտենհեմի» գլխավոր մարզչի պաշտոնում նշանակվել է Իգոր Տուդորը
«Տոտենհեմի» գլխավոր մարզչի պաշտոնում նշանակվել է Իգոր Տուդորը
 Թրամփի զինակիցը կոչ է արել նրան Ուկրաինա «Tomahawk» հրթիռներ մատակարարել
Թրամփի զինակիցը կոչ է արել նրան Ուկրաինա «Tomahawk» հրթիռներ մատակարարել
 Մյունխենի «Բավարիան» հաղթեց «Վերդերին»․ Լեվերկուզենի «Բայերը»՝ «Սանկտ Պաուլիին»
Մյունխենի «Բավարիան» հաղթեց «Վերդերին»․ Լեվերկուզենի «Բայերը»՝ «Սանկտ Պաուլիին»
 Մայր Աթոռը՝ Գարեգին Երկրորդի նկատմամբ քրեական հետապնդման մասին
Մայր Աթոռը՝ Գարեգին Երկրորդի նկատմամբ քրեական հետապնդման մասին
 Ես երբեք նման ֆուտբոլիստի չեմ հանդիպել․ Բուֆոնը՝ Ռոնալդուի մասին
Ես երբեք նման ֆուտբոլիստի չեմ հանդիպել․ Բուֆոնը՝ Ռոնալդուի մասին
 Հայ հայտնիների անցնող շաբաթն Ինստագրամում
Հայ հայտնիների անցնող շաբաթն Ինստագրամում
 Ռուսաստանի ՊՆ-ն հայտնել է Ուկրաինայի զինված ուժերի սպառազինության կենտրոնական բազայի հարվածման մասին
Ռուսաստանի ՊՆ-ն հայտնել է Ուկրաինայի զինված ուժերի սպառազինության կենտրոնական բազայի հարվածման մասին
 2026թ․ ՖԻՖԱ-ի աշխարհի առաջնության տոմսեր ունեցող անձինք կարող են ԱՄՆ վիզայի հարցազրույցի օր ամրագրել արտահերթ. Դեսպանատուն
2026թ․ ՖԻՖԱ-ի աշխարհի առաջնության տոմսեր ունեցող անձինք կարող են ԱՄՆ վիզայի հարցազրույցի օր ամրագրել արտահերթ. Դեսպանատուն
 Եվրամիությունում հնարավոր են համարել ԵՄ-ին Ուկրաինայի անդամակցության հնարավորությունը մինչեւ 2027թ.
Եվրամիությունում հնարավոր են համարել ԵՄ-ին Ուկրաինայի անդամակցության հնարավորությունը մինչեւ 2027թ.
 Բռնի տեղահանված անձանց առնչությամբ քննարկումները և հաղորդակցությունը պետք է ունենան բավարար զգայունություն․ ՄԻՊ
Բռնի տեղահանված անձանց առնչությամբ քննարկումները և հաղորդակցությունը պետք է ունենան բավարար զգայունություն․ ՄԻՊ
 Գյումրու հիվանդանոց է տեղափոխվել 10-ամյա աղջնակի մարմին, ով տանը սնունդ ընդունելիս խեղդամահ է եղել
Գյումրու հիվանդանոց է տեղափոխվել 10-ամյա աղջնակի մարմին, ով տանը սնունդ ընդունելիս խեղդամահ է եղել
 Ալիեւը Մյունխենում հանդիպել է Զելենսկու հետ
Ալիեւը Մյունխենում հանդիպել է Զելենսկու հետ
 Արմավիրի մարզում առևանգված 15-ամյա աղջկա հարազատները դիմում են իրավապահներին՝ պահանջելով գտնել երեխային
Արմավիրի մարզում առևանգված 15-ամյա աղջկա հարազատները դիմում են իրավապահներին՝ պահանջելով գտնել երեխային
 Հայաստանի Մ-19 հավաքականի կազմը
Հայաստանի Մ-19 հավաքականի կազմը
 TRIPP երթուղին ԱՄՆ նախագահի անունով անվանակոչելը ցույց է տալիս դրա նշանակությունը ԱՄՆ ներկայիս վարչակազմի համար․ Ալիև
TRIPP երթուղին ԱՄՆ նախագահի անունով անվանակոչելը ցույց է տալիս դրա նշանակությունը ԱՄՆ ներկայիս վարչակազմի համար․ Ալիև
 Վրաց-ռուսական սահման տանող ճանապարհին վերականգնվել է ծանր բեռնատարների երթևեկությունը
Վրաց-ռուսական սահման տանող ճանապարհին վերականգնվել է ծանր բեռնատարների երթևեկությունը
 Սևան-Երևան ավտոճանապարհին 28-ամյա վարորդը «Tesla»-ով դուրս է եկել ճանապարհի երթևեկելի գոտուց, բախվել երկաթե արգելապատնեշներին, բետոնե հենասյուներին և հայտնվել ձորում
Սևան-Երևան ավտոճանապարհին 28-ամյա վարորդը «Tesla»-ով դուրս է եկել ճանապարհի երթևեկելի գոտուց, բախվել երկաթե արգելապատնեշներին, բետոնե հենասյուներին և հայտնվել ձորում
 Մենք ընդամենը վեց ամիս է, ինչ խաղաղության մեջ ենք ապրում․ Ալիև
Մենք ընդամենը վեց ամիս է, ինչ խաղաղության մեջ ենք ապրում․ Ալիև
 Պենտագոնը արհեստական բանականություն է օգտագործել Մադուրոյին բռնելու համար. WSJ
Պենտագոնը արհեստական բանականություն է օգտագործել Մադուրոյին բռնելու համար. WSJ
 Այսօր տեղի ունեցավ աննախադեպ մի բան` քրեական հետապնդում հարուցվեց Ամենայն Հայոց Հայրապետի դեմ․ Նարեկ Կարապետյան
Այսօր տեղի ունեցավ աննախադեպ մի բան` քրեական հետապնդում հարուցվեց Ամենայն Հայոց Հայրապետի դեմ․ Նարեկ Կարապետյան Դատախազությունը քրեական հետապնդում է հարուցել Ամենայն Հայոց Կաթողիկոսի նկատմամբ
Դատախազությունը քրեական հետապնդում է հարուցել Ամենայն Հայոց Կաթողիկոսի նկատմամբ
 Մյունխենում հանդիպել են Վլադիմիր Զելենսկին և Իլհամ Ալիեւը
Մյունխենում հանդիպել են Վլադիմիր Զելենսկին և Իլհամ Ալիեւը
 Բռնցքամարտի Հայաստանի չեմպիոնները
Բռնցքամարտի Հայաստանի չեմպիոնները
 Ռուբիոն քննադատել է «աշխարհ առանց սահմանների» գաղափարը
Ռուբիոն քննադատել է «աշխարհ առանց սահմանների» գաղափարը
 Հանրապետության առանձին շրջաններում սպասվում են տեղումներ, լեռնային որոշ հատվածներում՝ նաև բուք
Հանրապետության առանձին շրջաններում սպասվում են տեղումներ, լեռնային որոշ հատվածներում՝ նաև բուք
 Գյումրիի դպրոցականները ՄԻՊ-ի հետ հանդիպմանը բարձրացրել են մի շարք հարցեր
Գյումրիի դպրոցականները ՄԻՊ-ի հետ հանդիպմանը բարձրացրել են մի շարք հարցեր
 Վթար՝ Եղեգնաձորում, բախվել են «Opel» ու «Toyota», վիրավոր կա
Վթար՝ Եղեգնաձորում, բախվել են «Opel» ու «Toyota», վիրավոր կա
 Վարդենյաց լեռնանցքը երեկվանից փակ է բոլոր տեսակի տրանսպորտային միջոցների համար
Վարդենյաց լեռնանցքը երեկվանից փակ է բոլոր տեսակի տրանսպորտային միջոցների համար
 Վթար՝ Եղեգնաձորում, բախվել են «Opel» ու «Toyota», վիրավnր կա․ Shamshyan
Վթար՝ Եղեգնաձորում, բախվել են «Opel» ու «Toyota», վիրավnր կա․ Shamshyan
 Քաղաքականություն ենք մտնում՝ հայակենտրոն ու բազմավեկտոր ուղեգիծ ձևավորելու համար․ Ավետիք Չալաբյան
Քաղաքականություն ենք մտնում՝ հայակենտրոն ու բազմավեկտոր ուղեգիծ ձևավորելու համար․ Ավետիք Չալաբյան Հունգարիայի վարչապետն արձագանքել է Զելենսկու՝ Օրբանը «փոր է աճեցնում» վիրավորանքին
Հունգարիայի վարչապետն արձագանքել է Զելենսկու՝ Օրբանը «փոր է աճեցնում» վիրավորանքին






